19.5 Attacks on cryptographic protocols
Recall from Chapter 2 Secure Channel and the CIA Triad, that a cryptographic protocol is a distributed algorithm defined by a sequence of steps precisely specifying the actions required of two or more entities to achieve a specific cryptographic goal [117].
Attacks on cryptographic protocols typically do not attack the cryptographic primitives they are built of, but the sequence of messages making up the protocol. An attack on a protocol is considered successful if any of the cryptographic goals of the protocol (confidentiality, entity authenticity, or message authenticity) are endangered.
19.5.1 Impersonation attacks
An impersonation attack is any deception attempt where Mallory claims to be another entity, say, Bob. What Mallory technically does to trick Alice into believing she is talking to Bob depends on the technical solution used by Alice to verify the identity of her communication peers. Popular examples of such mechanisms, which we also covered in previous chapters, are passwords, secret keys, and digital certificates.
While impersonation attacks are an immediate threat to entity authentication, in many practical scenarios, the ultimate goal of an impersonation attack is to compromise authorization and access control. While authorization is a security objective that ensures that the policy defining which user is allowed to do what on a given system is adhered to, access control ensures that only authorized users can access the system’s resources.
As shown in Figure 19.9, if Mallory successfully tricks Alice into believing she is Bob, Alice will grant Mallory Bob’s privileges. As a result, Mallory will be able to access all resources that Bob can access and interact with the system in any way that Bob is authorized to do.
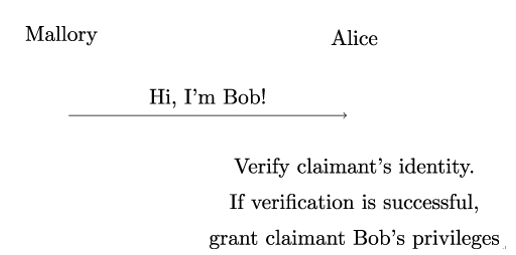
Figure 19.9: Working principle of an impersonation attack
19.5.2 Man-in-the-middle attacks
In a man-in-the-middle attack, Mallory secretly places herself between Alice and Bob to either compromise the confidentiality or integrity of their communication. More precisely, Mallory interacts with the communication between Alice and Bob to either read or manipulate their (or insert her own) messages.
Most practical man-in-the-middle attacks work because Alice and Bob believe they are talking directly to each other while, in reality, Mallory sits between them and runs two separate communication sessions, one with Alice and one with Bob. As such, it is an active attack. We do not consider a scenario in which Eve sits between Alice and Bob, merely listening to their communication, to be a man-in-the-middle attack.
We have already encountered an important example of a man-in-the-middle attack in Figure 7.3.
Recall from Chapter 7, Public-Key Cryptography, that using the Diffie-Hellman protocol, Alice and Bob establish a shared secret k over an insecure communication channel using the following protocol steps:
- Alice and Bob publicly agree on a cyclic group 𝔾 and a corresponding generator g.
- Alice chooses a natural number α, where 1 < α < N, where N is the order of G. α is Alice’s Private Key SKAlice. She must not disclose this number to any other party.
- Bob does the same as Alice: he independently chooses a number 1 < β < N as his private key SKBob.
- Alice computes A = gα in G and sends A to Bob. The number A (together with G and g) can be seen as Alice’s public key: PKAlice = (g,G,A).
- Bob computes B = gβ in G and sends B to Alice. The number B (together with G and g) can be seen as Bob’s public key: PKBob = (g,G,B).
- Alice computes KA = Bα. Bob computes KB = Aβ. However, both compute the same value k, because
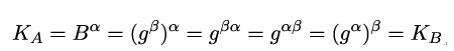
Leave a Reply